34+ intrusion detection system diagram
It has become increasingly important in mobile computingThe security of personal and business information now stored on smartphones is of particular concern. A unique host-based intrusion detection system HIDs is available on the service offering platform but is not available on the corporate network.

Fire Alarm System Electrical Engineering World Fire Alarm System Fire Alarm Home Security Systems
CPU System Chipset temperature detection CPU System Pump fan speed detection CPU System Pump fan speed control Form Factor ATX Form Factor 12 in.
. Buildings or portions thereof shall be provided with a means of egress system as required by this chapter. One of the first uses of the term protocol in a data-commutation context occurs in a memorandum entitled A Protocol for Use in the NPL Data Communications Network written by Roger Scantlebury and Keith Bartlett in April 1967. Intrusion Movement detection Presence detection Person localization.
Mobile security or mobile device security is the protection of smartphones tablets and laptops from threats associated with wireless computing. The Lenovo ThinkSystem SR655 is a 1-socket 2U server that features the AMD EPYC 7002 Rome and AMD EPYC 7003 Milan families of processors. More and more users and businesses use smartphones to communicate.
305 cm x 244 cm BIOS Features 1x 256 Mb flash UEFI AMI BIOS ACPI 60 SMBIOS 28 Multi-language Software Drivers DRAGON CENTER. Sections 1003 through 1030 shall apply to new. Up to four tamper pins for static and dynamic intrusion detections Data Flash Optimized for secure storage Address and data scrambling with user-defined key optional Rapid tamper erase on scrambling key and on one user-defined row.
The following diagram shows the default ports in a Workload Security system. MLX90640 32x24 IR array. With up to 64 cores per processor and support for the PCIe 40 standard for IO the SR655 offers the ultimate in single-socket server performance.
Information systems can be defined as an integration of components for collection storage. Up to four tamper pins for static and dynamic intrusion detections Data Flash Optimized for secure storage Address and data scrambling with user-defined key optional Rapid tamper erase on scrambling key and on one user-defined row. Soil to beef transfer factor TF beef daykg beef.
There are many reasons or causes for anomalies including system failures. Task people structure or roles and technology. 34 MHz RC oscillator Storage RAM Vss Vdd Figure 1 Block diagram.
TF beef is determined by the following equation for chemicals 25 x 10-8 K ow taken from McKone 1994. An information system IS is a formal sociotechnical organizational system designed to collect process store and distribute information. Mandatory ports refer to ports that must be opened to ensure the proper functioning of the Workload Security system.
From a sociotechnical perspective information systems are composed by four components. This product guide provides essential pre-sales information to. For details see the table below the diagram.
Element for intelligent building air conditioning Thermal Comfort sensor in automotive Air Conditioning control system Microwave ovens Industrial temperature control of moving. Service Provider Hybrid A control that makes use of both corporate controls and additional. The provisions of this chapter shall control the design construction and arrangement of means of egress components required to provide an approved means of egress from structures and portions thereof.
Anomaly detection refers to the task of identifying abnormal data that are significantly different from the majority of instances and has many important applications including industrial product defect detection infrastructure distress detection and medical diagnosis. Soil to milk transfer factor TF dairy daykg milk. On the ARPANET the starting point for host-to-host communication in 1969 was the 1822 protocol which defined.
TF dairy is determined by the following equation 79 x 10-9 K ow taken from McKone 1994Values for metals come from BAES IAEA NCRP and OTHER.

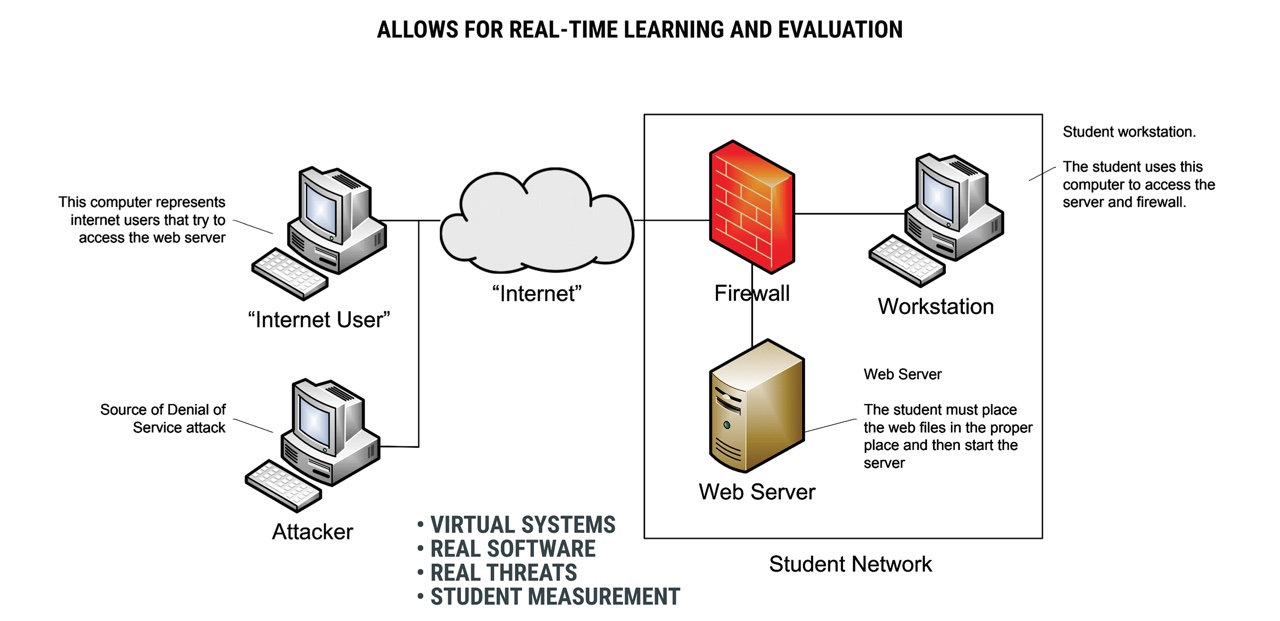
Cyrin Resources

Athenalarm Network Alarm Monitoring System In 2022 Alarm Monitoring Alarm System Security Solutions

What Is An Intrusion Detection System And The Types Of It Detection System Id Software

Framework Ids Ips Linux Security Pytbull Ids Ips Testing Pytbull Is An Intrusion Detection Prevention Security Tools Framework Web Security

Basics Of Intrusion Detection System Classifactions And Advantages System Detection Electronics Basics

Fire Alarm Addressable System Wiring Diagram Pdf New System Sensor Smoke Detector Wiring Diagram Simple Sys Fire Alarm System Fire Alarm Fire Protection System

Electronic Security System Importance Classifications And Working Electronic Security Systems Security System Electronics Basics

Types Of Fire Alarm Systems And Their Wiring Diagrams Fire Alarm System Fire Alarm Alarm System

Basics Of Intrusion Detection System Classifactions And Advantages System Detection Electronics Basics

Types Of Ids Behavioral Analysis Content Analysis Analysis
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile
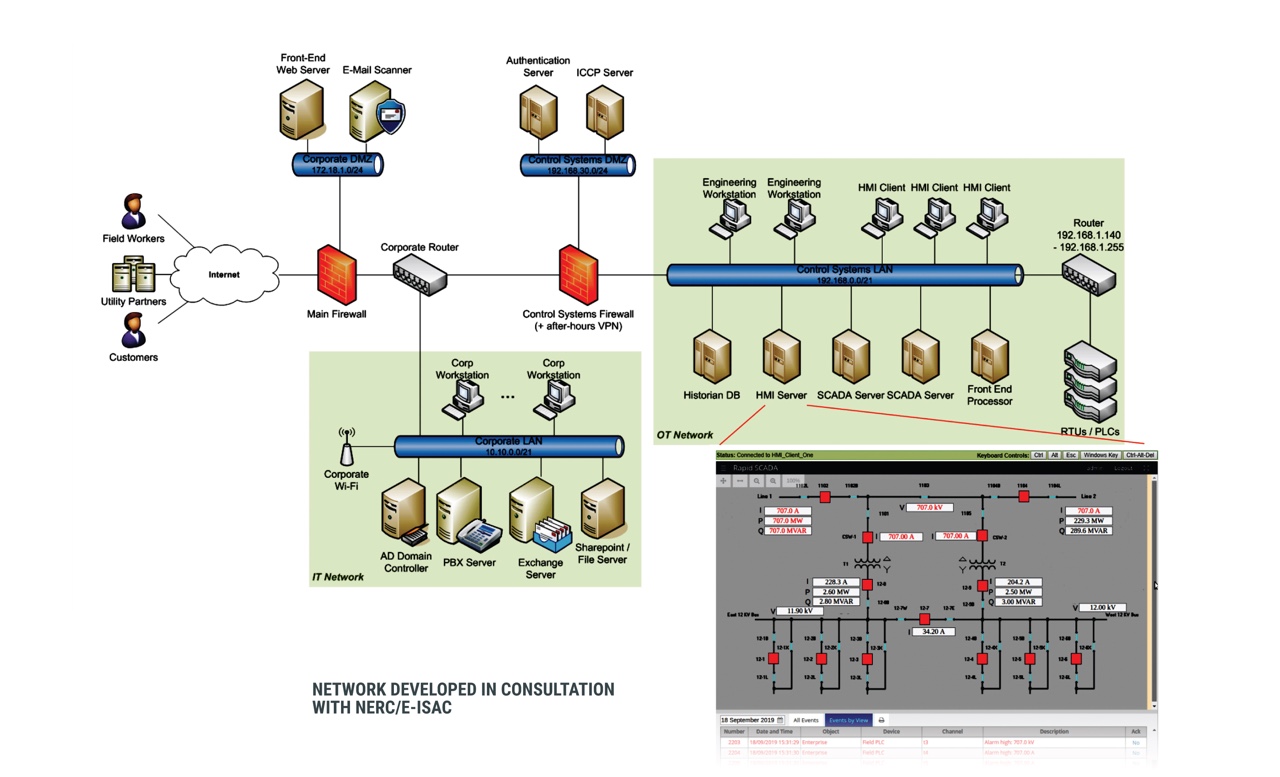
Cyrin Resources
A Survey Of Artificial Intelligence Techniques For Cybersecurity Improvement Document Gale Academic Onefile

Probemanager Centralize Management Of Intrusion Detection System Like Suricata Bro Ossec Software Development Hobby Shops Near Me Detection

Laser Security System Security System Security Alarm Home Security Systems

Ids Vs Ips Ipwithease Network Performance Networking Detection

Computer Security And Pgp What Is Intrusion Detection System Detection Computer Security Network Infrastructure